
Marketing automation platforms process vast amounts of sensitive data, making robust security measures essential. Here's a quick breakdown of how these platforms protect your data:
For industries like finance and healthcare, these measures aren't just protective - they're required to avoid legal penalties and reputational damage. Platforms like Visora integrate these practices with AI-driven tools, ensuring security without compromising functionality.
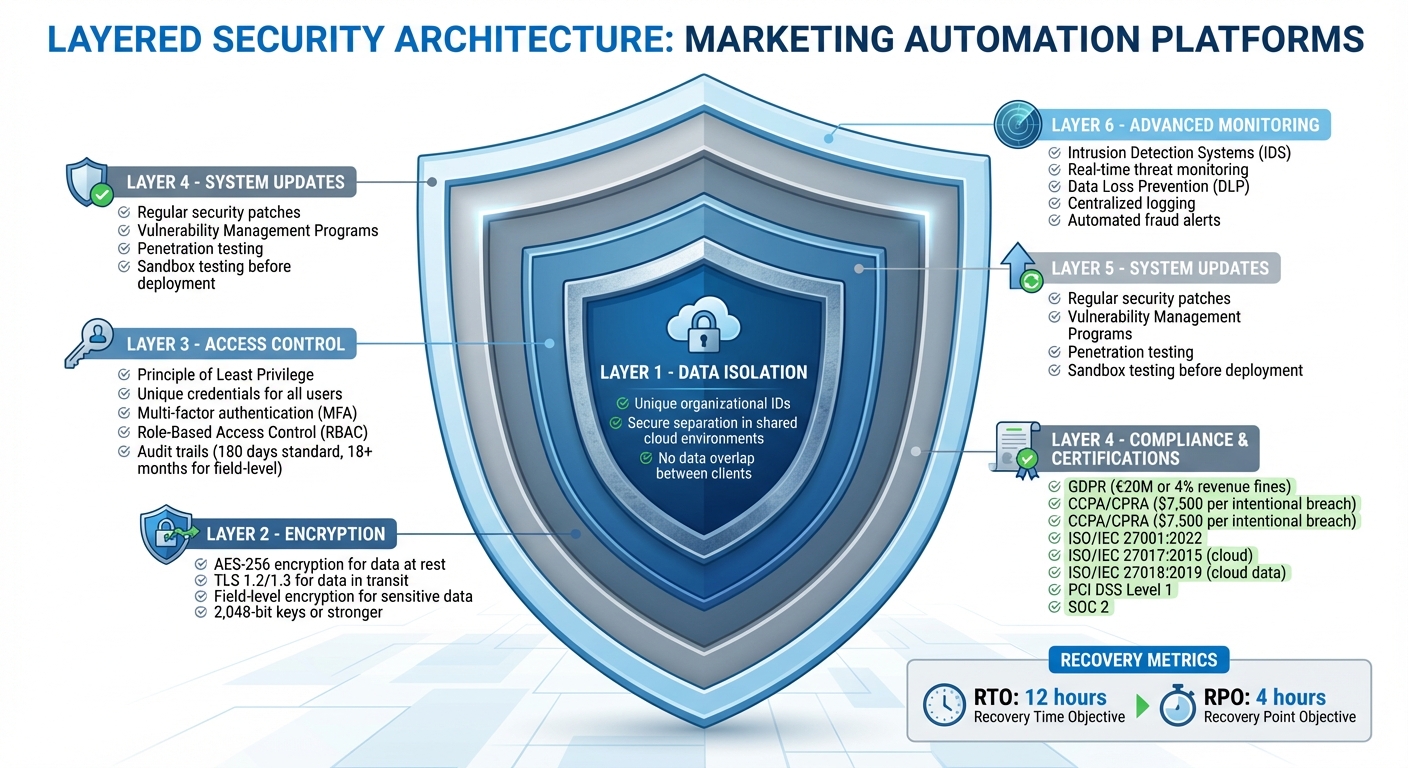
6 Core Security Layers in Marketing Automation Platforms
To maintain strict control in shared environments, marketing automation platforms rely on essential security measures like encryption, access controls, and regular system updates to safeguard sensitive data effectively.
Marketing automation platforms embrace a multi-layered security approach to protect customer data at every stage [2][5]. This strategy ensures that if one layer of defense is compromised, others remain intact to prevent breaches.
When data is in transit, session and security cookies play a key role. These cookies authenticate users and securely transfer information between browsers and servers [1]. For data stored in databases, platforms utilize field-level tracking to monitor changes to sensitive records. Some systems retain this audit data for a minimum of 18 months, while others store it indefinitely to create a comprehensive accountability trail [1].
Platforms often operate on private and public cloud infrastructures like AWS and Hyperforce. To identify and address vulnerabilities, these environments undergo regular penetration testing and vulnerability management [6][7]. Compliance with international standards, such as ISO/IEC 27001:2022 for Information Security Management and ISO/IEC 27018:2019 for Cloud Data Protection, ensures that encryption practices meet stringent global requirements [6][7].
This robust encryption framework lays the groundwork for the access control measures discussed below.
Access control policies are built around the Principle of Least Privilege, which ensures users are granted only the permissions necessary to perform their tasks. As Salesforce explains:
The Principle of Least Privilege states that each user or other entity must have only the minimum level of permissions that are necessary to get the job done [1].
This principle minimizes risks from insider threats or compromised accounts. Every user, including integration partners, is required to have unique credentials, eliminating the risks associated with shared passwords. This setup allows all actions to be traced back to specific individuals, simplifying the process of identifying suspicious activity [1].
Administrators can review login histories and audit trails, with records maintained for 6 days and 180 days respectively, to detect and respond to unusual activity [1]. Additionally, for sensitive data, platforms offer field-level audit trails that can retain change logs for 18 months or more [1].
Testing new user roles and permissions happens in sandbox environments, which are isolated from live systems. This ensures that any configuration errors do not compromise real customer data [1].
Regular system updates and patches are crucial for addressing newly discovered vulnerabilities. Marketing automation platforms implement dedicated Vulnerability Management Programs to systematically identify, track, and resolve security risks across their infrastructure [6][7]. These efforts are closely coordinated with cloud providers like AWS and Hyperforce to ensure consistent patching across all environments [6][7].
To validate the effectiveness of these patches, platforms conduct external security assessments, including penetration testing [7]. Before updates are deployed to live systems, they are rigorously tested in sandbox environments and tracked via audit trails to avoid introducing new vulnerabilities [1].
Documentation for these programs is kept up-to-date, with the most recent vulnerability management overviews and penetration test summaries refreshed as recently as January 2026 [6][7]. These proactive update practices form a critical layer of the broader security strategy outlined above.
Marketing automation platforms operate under strict regulatory frameworks, with severe penalties for breaches. These regulations not only fulfill legal obligations but also play a crucial role in ensuring data security - a key factor in maintaining B2B growth. Let’s take a closer look at some major regulations and the certifications that validate a platform's compliance.
The General Data Protection Regulation (GDPR) applies to any organization processing the data of EU residents, no matter where the company is based [8][9]. GDPR mandates technical measures like encryption and pseudonymization to safeguard personal data. Article 32 of GDPR emphasizes:
"The processor shall implement appropriate technical and organisational measures to ensure a level of security appropriate to the risk, including... the pseudonymisation and encryption of personal data" [8].
Failure to comply can lead to fines as high as 4% of annual global revenue or €20 million - whichever is greater. Additionally, organizations must promptly inform affected individuals if a breach poses significant risks to their rights [8][9].
In the U.S., the California Consumer Privacy Act (CCPA) and its update, the California Privacy Rights Act (CPRA), give California residents control over their personal data [9]. Unlike GDPR, which requires explicit consent, CCPA uses an opt-out model, featuring tools like "Do Not Sell or Share My Personal Information." The law also includes a 12-month look-back period, obligating businesses to disclose how personal data was collected and used in the previous year [9].
Violations of CCPA can result in fines of $7,500 per intentional breach, and consumers may receive up to $750 per incident in civil damages for breaches involving unencrypted data [8][9]. Both GDPR and CCPA offer a "safe harbor" for encrypted data - if encryption keys remain secure, companies may avoid notifying individuals about breaches since the data would be unreadable to unauthorized parties [8].
Marketing automation platforms generally act as "data processors", meaning they handle data on behalf of their clients. For example, Salesforce highlights this role:
"Trust is our #1 core value and as a data processor, we implement robust security measures to protect the confidentiality, integrity, and availability of our customer data."
- Salesforce [2]
This distinction clarifies that while platforms must enforce strong security protocols, customers are ultimately responsible for how the data is used. To complement these regulations, certifications provide additional assurance of a platform's security standards.
Certifications serve as third-party endorsements of a platform's security practices. For example, ISO/IEC 27001:2022 is the global standard for Information Security Management Systems (ISMS), outlining a systematic approach to protecting sensitive data [6][4]. Many platforms also maintain certifications like ISO/IEC 27017:2015 for cloud-specific controls and ISO/IEC 27018:2019 for safeguarding personal data in public clouds [6][7][4][10]. These certifications, updated regularly, are supported by practices like vulnerability management, penetration testing, and external security assessments [6][7][10].
In addition to international standards, platforms often secure region-specific certifications to meet local requirements. For instance, the HDS (Hébergeur de Données de Santé) certification allows for hosting healthcare data in France, while C5 addresses cloud security standards in Germany. In the financial sector, PCI DSS Level 1 compliance ensures the protection of payment card data [3]. Many platforms also participate in frameworks like the EU-U.S. Data Privacy Framework to facilitate compliant cross-border data transfers [3].
B2B decision-makers should carefully review a platform's Service Provider Agreement (SPA) for up-to-date certifications [6][4]. Key certifications to look for include ISO 27001 for overall security, ISO 27017 for cloud-specific measures, and ISO 27018 for protecting personal data in the cloud [7][10]. Additionally, platforms should have documented Third-Party Risk Management programs to ensure data security when working with sub-processors [6][7].
Building on a foundation of compliance and core security measures, advanced tools provide an additional layer of protection to ensure data remains secure and intact.
Modern platforms utilize Intrusion Detection Systems (IDS) to actively monitor network traffic and hosts for any unauthorized access attempts. As Salesforce highlights, "Salesforce, or an authorized third party, will monitor the Covered Services for unauthorized intrusions using network-based and/or host-based intrusion detection mechanisms" [3]. These systems work in real time, analyzing activity patterns to detect anomalies like unusual login locations or multiple failed authentication attempts. Real-time browser analysis further strengthens security by identifying compromised browsers and blocking fraudulent login attempts.
To support these efforts, all security events are logged in centralized systems. This centralized logging not only facilitates ongoing monitoring but also allows for detailed forensic analysis in the event of a breach. By maintaining a thorough record of user actions, organizations can swiftly identify and respond to potential threats while ensuring accountability.
Another critical best practice is avoiding shared credentials. Instead, assign unique accounts to each user and integration partner. This approach ensures that individual actions can be tracked and access can be immediately revoked if an account is compromised. Together, these monitoring strategies create a proactive defense against data breaches and reinforce privacy from the outset.
Data Loss Prevention (DLP) strategies are designed to stop sensitive information from being unintentionally exposed or removed from the system. Platforms often employ tools like Field Audit Trails, which log every change made to data fields. This creates a historical record that shows when and how data was accessed or altered - an invaluable resource, especially in systems where prospect data passes through multiple stages, from initial contact to final deal closure.
Privacy by design principles are baked directly into the architecture of many platforms. For instance, multitenant systems use unique organizational IDs to keep customer data securely separated, ensuring no overlap between clients. Disaster recovery measures are also prioritized, with leading platforms aiming for a Recovery Time Objective (RTO) of 12 hours and a Recovery Point Objective (RPO) of 4 hours. This ensures that systems can be restored quickly with minimal data loss in the event of an incident.
For API integrations, Mutual TLS (mTLS) offers an additional layer of security by providing two-way authentication. Both the platform and the receiving server verify each other's identity before exchanging data. To avoid integration failures, platforms automate certificate management, reissuing public certificates 60 days before they expire and revoking them 30 days prior to expiration.
To complement data protection measures, secure communication channels are essential for safeguarding information as it moves across networks. Virtual Private Networks (VPNs) and encrypted transport protocols ensure end-to-end protection during data transmission. Platforms implement technologies like Transport Layer Security (TLS) and Internet Protocol Security (IPsec) to maintain confidentiality. For example, Microsoft Azure adheres to IEEE 802.1AE MAC Security Standards and uses 256-bit AES encryption that complies with FIPS 140-2 standards across its extensive network of over 150 datacenters in more than 60 regions worldwide.
For businesses integrating marketing automation with CRM or sales systems, private connectivity solutions like Salesforce Private Connect create secure links between cloud environments without relying on public internet routes. After authentication, platforms generate random session IDs stored in the browser to secure session states.
Visora takes a proactive approach to data security, combining advanced measures with industry best practices to support B2B growth and protect client information.
Client data protection is at the core of Visora's AI-powered CRM systems. All data at rest is encrypted using 256-bit AES encryption, adhering to FIPS 140-2 standards [12]. When data is transferred - whether through API calls or authenticated sessions - TLS 1.2 or 1.3 with 2,048-bit keys or stronger ensures secure communication [13].
To add another layer of security, Visora employs field-level encryption for sensitive information. This means that specific data fields containing confidential details are encrypted individually, limiting access to only authorized users [13]. Key management is handled through dedicated vaults, similar to Azure Key Vault, allowing clients to choose between service-managed or customer-managed encryption keys [12].
For further security, Visora uses mTLS (mutual TLS) for outbound API connections, ensuring both parties verify their identities before any data exchange. This is especially critical when integrating with financial systems or third-party data providers [11].
Visora's sales automation tools are built to comply with major data protection regulations, providing peace of mind during multi-channel outbound campaigns. The platform aligns with GDPR requirements for EU-based prospects and CCPA standards for California residents [14][15].
To detect and prevent potential threats, real-time intrusion detection systems (IDS) and automated fraud alerts monitor activity and flag any suspicious behavior [15][16]. Additionally, users receive automated login notifications to help prevent identity theft and unauthorized access [15].
"Data security is no longer the responsibility of any single entity within an organization - it's a critical business imperative shared by all departments." – Adverity [16]
Comprehensive audit logs track every system interaction, providing a full record of activities. These logs are invaluable for resolving disputes, ensuring compliance, and meeting regulatory requirements. For instance, under GDPR, businesses must report certain data breaches within 72 hours of discovery - detailed audit trails make this process significantly smoother [15][16].
Visora's secure systems have played a pivotal role in helping organizations protect data while driving revenue growth. Here are a few examples:
These examples highlight how Visora’s focus on security and compliance directly supports B2B growth, ensuring clients can pursue opportunities without compromising data integrity.
Data security is the backbone of trust for B2B leaders and their marketing automation platforms. Whether you're managing sensitive client details, financial records, or strategic partnership data, strong security measures are essential to ensure confidentiality, integrity, and availability.
The best platforms go beyond basic protections by implementing layered defenses, such as 256-bit encryption, multi-factor authentication, real-time threat monitoring, and audit trails. Additionally, adhering to the Principle of Least Privilege helps limit user access, reducing the risk of compromised accounts and fostering accountability across the organization.
For industries like finance, real estate, and professional services, compliance with regulations like GDPR and CCPA, as well as certifications such as ISO 27001 and SOC 2, is non-negotiable. These standards provide independent verification that a platform is committed to safeguarding your data through rigorous monitoring and security practices.
Visora stands out as a prime example of how cutting-edge technology and robust security can work together to support reliable B2B growth. By combining AI-driven growth tools with enterprise-level security measures, Visora ensures that every CRM interaction, acquisition campaign, and partnership is protected by the same high standards trusted by Fortune 500 companies. For B2B leaders, strong security isn't just about reducing risk - it's about paving the way for sustainable and confident growth.
Marketing automation platforms take data security seriously, especially in shared cloud environments. They employ several key measures to protect sensitive information:
These platforms also align with industry standards like SOC 2 and adhere to regulatory frameworks designed to meet strict data protection requirements. By blending cutting-edge technology with rigorous compliance protocols, they work to keep your data safe and private.
Compliance standards such as GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) play a crucial role in ensuring data security within marketing automation platforms. These regulations establish specific rules for protecting personal information, including the use of encryption, pseudonymization, and secure storage practices.
They also require organizations to promptly inform users about any data breaches, promoting transparency and accountability. Following these standards not only helps marketing platforms protect user privacy but also strengthens customer trust.
Marketing automation platforms take data protection seriously, employing advanced security measures to keep sensitive information safe. They use encryption to secure data both when it’s stored and during transmission, effectively blocking unauthorized access. On top of that, these platforms actively monitor user activities - like logins, configuration updates, and other actions - to quickly catch anything out of the ordinary.
If a potential threat arises, automated systems spring into action. They might send out alerts, limit access, or initiate security protocols to reduce risks. Regular security audits and adherence to industry standards further strengthen their defenses. This layered strategy not only safeguards customer data but also provides businesses with much-needed peace of mind.