
Financial CRMs handle sensitive data like bank records and personal details, making secure data transmission a priority. Encryption protocols not only protect this information but are also required by regulations like GDPR, PCI DSS, and the FTC Safeguards Rule. Failing to comply can lead to breaches, lawsuits, and hefty penalties, as seen with Equifax and Cash App Investing.
Here’s a quick overview of the key protocols ensuring compliance and security:
Each protocol plays a role in safeguarding data, maintaining trust, and ensuring compliance with industry standards. The choice depends on your organization’s specific security and performance needs.
Transport Layer Security (TLS) 1.3 plays a key role in safeguarding data exchanged between financial CRM systems and their users. Introduced by the IETF in August 2018, it replaced TLS 1.2 and earlier versions with more advanced security features to better protect sensitive financial data [4].
TLS 1.3 uses only Authenticated Encryption with Associated Data (AEAD) algorithms, leaving behind older, less secure encryption methods. It also enforces forward secrecy by eliminating static RSA and Diffie-Hellman exchanges. This means that even if a server's long-term private key is compromised, session keys remain secure, ensuring past CRM data stays protected [4]. Additionally, once the "ServerHello" message is exchanged during the handshake, all subsequent messages, including sensitive metadata and certificates, are encrypted to prevent interception [4].
Server authentication in TLS 1.3 relies on asymmetric cryptography, using methods such as RSA, ECDSA, or EdDSA. It employs a CertificateVerify message to sign the handshake transcript and a Finished message to confirm endpoint identity [4][8]. For maximum security in financial applications, experts recommend using ECDSA-256 with SHA256 on the P-256 curve or 2,048-bit RSA with SHA256 for certificates [9].
"The primary goal of TLS is to provide a secure channel between two communicating peers... specifically, the secure channel should provide Authentication, Confidentiality, and Integrity." - IETF RFC 8446 [4]
TLS 1.3 supports compliance with major regulations, including PCI DSS Requirement 4, which mandates encryption of payment card data [10]. U.S. government systems were required to adopt TLS 1.3 by January 1, 2024, as outlined in NIST Special Publication 800-52 Revision 2 [6][7]. The protocol also aligns with UK GDPR and the Data (Use and Access) Act by ensuring secure transmission of personal data [5].
Deploying TLS 1.3 is simpler and more efficient than previous versions. It reduces handshake latency from two round-trips (in TLS 1.2) to a single round-trip, which not only boosts performance for financial CRM applications but also strengthens security [4]. To ensure proper implementation, online testing tools are available to verify your HTTPS setup and check for vulnerabilities like downgrade attacks [5].
Up next, we’ll look at HTTPS, another essential protocol for securing financial CRM data transmissions.
Hypertext Transfer Protocol Secure (HTTPS) merges standard HTTP with Transport Layer Security (TLS) to establish an encrypted connection between financial CRM systems and their users. It has become the go-to standard for safeguarding sensitive information like bank details, login credentials, and personal data during online transactions [1].
HTTPS relies on TLS 1.2 and TLS 1.3 protocols, which use cryptographic algorithms recommended by NIST and FIPS-based cipher suites [5][6]. Most modern implementations utilize AES-256 encryption, offering strong protection against brute-force attacks [1]. Even if data packets are intercepted, the encryption ensures they remain incomprehensible to unauthorized individuals.
To confirm secure connections, HTTPS uses digital certificates that verify the server’s identity and ensure the integrity of transmitted data [1]. Users can identify secure connections through the "https://" prefix and the lock icon displayed in their browser [1].
"Only when you see an https address can you be confident that your data is optimally protected during transmission and cannot be intercepted or manipulated by unauthorised parties." - Emrick Etheridge, Information Security Expert, DataGuard [1]
HTTPS plays a key role in meeting financial regulations. For instance, PCI DSS Requirement 4 mandates encrypting cardholder data sent over public networks [10]. The protocol also supports GDPR compliance by protecting sensitive customer information and preventing unauthorized access [1]. With 78% of Americans prioritizing data privacy but only 20% fully trusting companies to safeguard their information, implementing HTTPS is critical for earning customer trust [11].
For users, adopting HTTPS is seamless [5]. However, server administrators must configure secure cipher suites for high-security needs and enable HTTP Strict Transport Security (HSTS) to ensure all connections default to HTTPS [5]. Redirects from HTTP to HTTPS should be set up on the server side, and regular monitoring of security certificates is necessary to maintain a reliable public-key infrastructure [5].
Next, we’ll look at SFTP and its role in secure file transfers within financial systems.
Secure File Transfer Protocol (SFTP) is a method that uses SSH to transfer CRM files securely. Unlike standard FTP, which sends data and credentials in plain text, SFTP encrypts both commands and data, making it much harder for attackers to intercept or manipulate information.
SFTP relies on the Advanced Encryption Standard (AES), offering key strengths of 128, 192, and 256 bits. Most modern systems use AES‑256, which is widely regarded as the gold standard for high-security applications, including financial CRM systems and U.S. government data protection [1][12].
SFTP supports two primary authentication methods: passwords and SSH keys. SSH key-based authentication uses asymmetric encryption with public and private key pairs, providing a much stronger defense against brute-force attacks. To comply with the FTC Safeguards Rule, financial institutions are required to implement multi-factor authentication, combining at least two methods - such as a password, token/SSH key, or biometrics. This aligns with PCI DSS Requirement 8, which mandates unique IDs for every user.
"A financial institution's information security program is only as effective as its least vigilant staff member." - FTC Safeguards Rule [3]
SFTP satisfies PCI DSS Requirement 4 by encrypting cardholder data when transmitted over public networks [10]. It also meets the FTC Safeguards Rule under the Gramm-Leach-Bliley Act, which mandates encryption of customer information both in transit and at rest. Since SFTP inherently encrypts data during transfer, it fulfills the "in transit" requirement. Additionally, the rule requires financial institutions to notify the FTC within 30 days if a breach exposes unencrypted data affecting at least 500 consumers, highlighting the importance of secure file transfers [3].
While SFTP offers robust security, its effectiveness depends on proper setup and management. Organizations should prioritize SSH key-based authentication over password-only methods to minimize the risk of credential theft. When an employee with access leaves the organization, administrators must revoke their SSH keys immediately and update system configurations. Regular security measures, such as annual penetration tests and vulnerability assessments every six months, help ensure compliance with financial security standards and maintain a secure file transfer environment [3].
With SFTP covered, the next section explores OAuth 2.0 for managing CRM authorization.
OAuth 2.0 is an authorization framework designed to replace traditional password-sharing methods with short-term access tokens. These tokens allow financial CRM systems to provide limited, scoped access to specific resources for a set period, significantly reducing the chances of credential theft or unauthorized access[14].
OAuth 2.0 uses tokens that are tied to the sender, ensuring that only the intended client can utilize the token. To counter authorization code injection attacks, many modern systems implement PKCE (Proof Key for Code Exchange) with S256 hashing[13]. Financial platforms increasingly favor asymmetric cryptography methods, such as Private Key JWT or Mutual TLS, over shared secrets. For robust security, RSA keys should be at least 2,048 bits long, while elliptic curve keys should have a minimum of 160 bits[15].
"OAuth is being used in environments with higher security requirements than considered initially, such as open banking, eHealth, eGovernment, and electronic signatures." - IETF RFC 9700[13]
OAuth 2.0 aligns with Open Banking standards and ISO 29100 privacy guidelines[16]. The Financial-grade API (FAPI) profile builds on OAuth 2.0 to address high-risk financial scenarios, such as those in commercial and investment banking. Under FAPI, credentials must be generated with at least 128 bits of entropy, and authorization codes are limited to a 60-second lifespan to minimize the risk of replay attacks[15][17].
Implementing OAuth 2.0 requires meticulous attention to detail. Organizations must enforce exact string matching for redirection URIs rather than allowing wildcard patterns, which could lead to authorization code leaks to malicious domains[13]. Deprecated grant types, such as Implicit Grant and Resource Owner Password Credentials Grant, should be avoided to reduce token exposure risks. Financial institutions are also encouraged to adopt Pushed Authorization Requests (PAR), which shift authorization parameters from browser URLs to secure server-to-server communications, thereby shrinking the attack surface[17].
Next, we’ll look at how IPsec VPN enhances the security of CRM network communications.
IPsec VPN establishes secure tunnels for all financial CRM traffic between endpoints. Unlike protocols designed for specific applications, IPsec encrypts every packet sent across the connection. This makes it a strong choice for transferring sensitive data such as customer records, bank account details, and tax information over public networks [18]. It works at the network layer, providing an added layer of security to complement application-level protocols.
IPsec VPNs rely on AES-256 encryption, which is highly resistant to brute-force attacks.
"Encryption serves as your first line of defence against data leaks" - Emrick Etheridge, Information Security Expert, DataGuard [1]
The Internet Key Exchange (IKE) protocol manages the configuration and key management for IPsec connections. It ensures security through encryption for confidentiality, integrity to prevent tampering, and authenticity using digital signatures and message authentication [18]. To maintain a secure system, financial institutions should adopt strong key management practices. This includes securely storing encryption keys, maintaining secure backups of master keys, and re-encrypting critical systems when employees with access to keys leave the organization.
IPsec VPN helps financial institutions comply with key industry regulations. For instance, it supports PCI DSS Requirement 4, which mandates encrypting payment card data transmitted over public networks. It also integrates with firewall architectures to meet PCI DSS Requirement 1, aimed at protecting cardholder data environments [10]. For federal guidelines, NIST SP 800-77 Rev. 1 offers best practices for deploying IPsec VPNs for sensitive data. Organizations processing over 6,000,000 card transactions annually (PCI DSS Level 1) face the most stringent compliance standards, making IPsec's network-wide protection particularly useful [10].
Setting up IPsec VPNs requires meticulous attention to detail. Security policies, key management protocols, and network-layer integration must all be properly configured [18]. Regularly patching VPN gateways and operating systems is crucial to address new vulnerabilities. Additionally, organizations must assign unique VPN user IDs to comply with PCI DSS Requirement 8 [10]. While IPsec's ability to secure all traffic, rather than just individual applications, adds complexity to its deployment, this broad protection makes it an excellent choice for safeguarding financial CRM systems.
AES-256 plays a key role in safeguarding data at rest within financial CRMs, building on secure transmission protocols. This symmetric encryption method uses a 256-bit key to transform sensitive information into unreadable ciphertext through 14 rounds of substitution, transposition, and mixing [19][20]. It’s so secure that the U.S. National Security Agency has approved it as the only publicly available cipher for protecting "Top Secret" information [19]. Let’s break down its encryption strength, key management, and compliance benefits.
With 2^256 possible combinations, AES-256 makes brute-force attacks practically impossible. Even the most advanced attack method, the biclique approach, would require 2^254.3 operations - still far out of reach [19][20].
One of the standout features of AES-256 is its resistance to quantum computing threats. While AES-128 offers only 64-bit security against quantum attacks, AES-256 maintains a robust 128-bit security level, making it a smart choice for financial institutions preparing for a post-quantum world [19][20].
AES-256 uses a single 256-bit key for both encrypting and decrypting data, which makes it highly efficient when handling large amounts of CRM data [19][20]. However, the strength of this encryption hinges on one critical element: key protection. Financial institutions often rely on Hardware Security Modules (HSMs) - tamper-proof devices designed to keep encryption keys safe from unauthorized access [12][22].
"Encryption can only be as good as the degree to which its associated keys are protected. If one does not protect the encryption keys, there is no point in encrypting the data – find the keys, access the data." - Entrust [22]
To enhance security, many organizations use a Key Management System (KMS) to centralize control and monitoring of encryption keys across CRM modules. Automating key rotation reduces the risk of vulnerabilities, and implementing separation of duties ensures that no single individual has complete control over key creation and usage [12].
AES-256 supports compliance with some of the most stringent financial regulations. Under GDPR Article 32, encryption is recognized as an effective measure to protect data [21]. For PCI DSS, AES-256 qualifies as strong encryption for safeguarding cardholder data, whether it’s stored or in transit [12][22]. Additionally, it meets FIPS 197 and FIPS 140-3 standards, which are often required for government contracts and high-security audits [19][22].
By implementing AES-256, organizations can also reduce compliance costs and audit complexities. For example, encryption can "de-scope" certain regulatory requirements by desensitizing data. This is particularly important given the rising cost of data breaches, which hit an average of $4.88 million in 2024 - a 10% increase from the previous year [12].
The biggest challenge with AES-256 lies in managing the entire key lifecycle, from secure generation to eventual destruction [12][22]. Losing an encryption key without a backup renders the encrypted data permanently inaccessible [12]. Insider threats also pose risks, as authorized users might mishandle or misuse keys [12].
"Weak keys are like rusty locks - they give a false sense of security. Always use cryptographically secure methods... to generate your keys." - Fletus Poston III, Senior Manager, Security Operations, CrashPlan [12]
To simplify implementation, financial institutions should automate key management processes to reduce human error. Cloud-based HSMs are an effective solution, eliminating the need for physical hardware maintenance [12][22]. Additionally, pairing AES-256 with Managed File Transfer (MFT) systems adds extra layers of security, such as multi-factor authentication and access controls, further strengthening the encryption framework [20].
AES-256 integrates seamlessly with secure transmission protocols, creating a robust security foundation for financial CRMs.
Mutual TLS (mTLS) builds upon standard TLS by requiring both the client and server to present X.509 certificates, proving ownership of their respective private keys[24]. This two-way authentication creates a trusted connection, making it ideal for financial CRM systems that handle sensitive customer data and high-stakes transactions.
While standard TLS focuses on authenticating only the server, mTLS takes it a step further by requiring the client to provide its own certificate for verification. This ensures "holder-of-key" security, meaning that even if an access token is intercepted, it can't be used without the matching private key[24]. Financial regulators often recommend mTLS for high-risk scenarios, such as when security administrators or customers are involved in critical transactions like wire transfers[23].
"Binding an access token to the client's certificate prevents the use of stolen access tokens or replay of access tokens by unauthorized parties." - RFC 8705[24]
For OAuth 2.0 implementations, mTLS strengthens security by binding tokens to certificates. Using the x5t#S256 confirmation method, the certificate's SHA-256 thumbprint is embedded into access tokens, allowing resource servers to verify that the token holder has the correct private key[24]. This approach not only enhances token security but also helps organizations meet stringent compliance requirements.
mTLS plays a key role in meeting various regulatory standards. It supports compliance with the Interagency Guidelines Establishing Information Security Standards and helps financial institutions fulfill USA PATRIOT Act requirements for verifying identities[23]. When paired with FIPS-compliant cipher suites and NIST-approved cryptographic algorithms, mTLS meets PCI DSS standards for strong encryption and multi-factor authentication by restricting access to devices with valid certificates[7].
For SOC 2 compliance, mTLS aligns with Trust Services Criteria for Security and Confidentiality by ensuring that data in transit is accessible only to authenticated endpoints. Additionally, starting January 1, 2024, NIST guidelines will require government TLS servers and clients to support TLS 1.3. In high-security environments, mTLS implementations are expected to use FIPS-based cipher suites to meet these updated standards[7].
While mTLS offers robust security and regulatory benefits, it also introduces operational challenges. Managing the lifecycle of client-side certificates - covering issuance, distribution, renewal, and revocation - can be complex, especially across numerous CRM endpoints[24]. Financial institutions need to maintain an inventory of APIs and systems requiring mTLS, including those from third-party cloud providers[23].
Automated PKI tools can help streamline certificate management, while real-time validation methods like Certificate Revocation Lists (CRLs) or the Online Certificate Status Protocol (OCSP) are essential for identifying compromised certificates. If load balancers or proxies handle TLS termination, securely passing client certificate details to backend systems is critical to preserve mTLS integrity[24].
To maintain security, organizations should implement automated monitoring for certificate expiration. Expired certificates can lead to immediate authentication failures, disrupting operations. As with earlier protocols, continuous monitoring and automation are key to ensuring the reliability and security of mTLS deployments[24].
WebSockets Secure (WSS) is a key protocol for enabling real-time communication in financial CRMs. It facilitates instant, bidirectional data exchange between CRM systems and their clients while leveraging the encryption strength of HTTPS. This makes it particularly suitable for applications like live trading dashboards, customer service chats, and real-time account notifications - where immediate data updates are critical.
WSS operates over TLS (on port 443) and uses AES-256 encryption to ensure data confidentiality and integrity. For optimal security, it’s recommended to implement TLS 1.2 or 1.3 with AES-256. As Matthew O'Riordan, CEO of Ably, explains:
"The wss scheme uses the same security mechanism as https to secure connections, while ws corresponds to http."
To protect against CRIME and BREACH attacks, disable the permessage-deflate compression extension unless absolutely necessary. Additionally, apply safeguards like rate limiting (e.g., 100 messages per minute) and set a maximum message size of 64 KB to prevent Denial-of-Service attacks and resource exhaustion.
Since WebSocket lacks built-in authentication, it's essential to enforce token-based controls during the initial HTTP handshake. Common methods include JSON Web Tokens (JWT) or HMAC signatures. For example, in May 2024, Coinbase updated its Advanced Trade WebSocket API to require JWT-based authentication for its Direct Market Data feed, with tokens expiring after 120 seconds to minimize hijacking risks.
To defend against Cross-Site WebSocket Hijacking (CSWSH), validate the Origin header against a strict allowlist. Enhance security further by revalidating sessions every 30 minutes and using ping/pong frames to detect dead connections. These measures align with regulatory requirements for secure, authenticated connections.
WSS supports compliance with key regulatory standards. For instance, it encrypts data as mandated by PCI DSS Requirement 4. Additionally, it helps meet SOC 2 requirements by providing encrypted and authenticated communication channels, contributing to the Trust Services Criteria for security and confidentiality.
Beyond securing the connection itself, implement message-level authorization to verify that each action - like executing trades or updating user data - is aligned with the user's roles and permissions. Since standard HTTP access logs only capture the initial WebSocket upgrade request, custom application-level logging is crucial for maintaining comprehensive audit trails and ensuring regulatory compliance.
Zero Trust Network Access (ZTNA) represents a significant change in how financial CRMs handle security. Unlike older, perimeter-based methods that inherently trust users inside the network, ZTNA operates on a core rule: never trust by default; always verify access. According to NIST SP 800-207:
"Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership."
This concept is particularly important for financial CRMs, where remote work, BYOD policies, and cloud-based systems have blurred traditional network boundaries. ZTNA builds on earlier encryption and access control measures by focusing on protecting specific resources - like individual services or data sets - rather than securing entire network segments. Every access request is authenticated and authorized for each session, whether the user is in the office or working remotely.
ZTNA relies on strong multi-factor authentication (MFA) for every session involving financial CRM resources. This typically involves at least two factors, such as a password combined with a token or biometric verification [3]. Beyond the initial login, ZTNA enforces the principle of least privilege, granting users session-based access limited to what they need for their specific tasks. This approach minimizes the risk of lateral movement within the network if credentials are compromised, offering an essential layer of protection for sensitive customer data.
ZTNA's strict authentication and access practices align with key regulatory requirements. For example, it supports PCI DSS Requirement 7 by limiting access to cardholder data strictly to business needs and satisfies Requirement 8 by ensuring each user has a unique ID for system access [25][10]. Additionally, ZTNA's continuous monitoring capabilities fulfill PCI DSS Requirement 10, which mandates tracking all access to network resources.
For financial institutions governed by the FTC Safeguards Rule, ZTNA's session-based verification and MFA protocols directly address the rule's call for administrative, technical, and physical safeguards. The rule also requires institutions to notify the FTC within 30 days of any breach involving unencrypted data from 500 or more consumers [3]. By enforcing granular access controls and encryption, ZTNA significantly reduces the likelihood of such breaches.
Shifting to ZTNA involves moving from network-based to identity- and resource-based security. This requires a detailed inventory of all data, devices, and platforms to ensure Zero Trust policies are applied effectively [3]. Legacy systems and third-party access can add layers of complexity to this process [23].
While the transition can be challenging, it’s an essential step. Organizations need to implement continuous monitoring to detect unauthorized access in real time, rather than relying on periodic security assessments [3]. Like AES-256 and TLS, ZTNA ensures data remains encrypted both at rest and in transit, with formal key management systems in place to avoid the risks of storing encryption keys as plain text files [1].
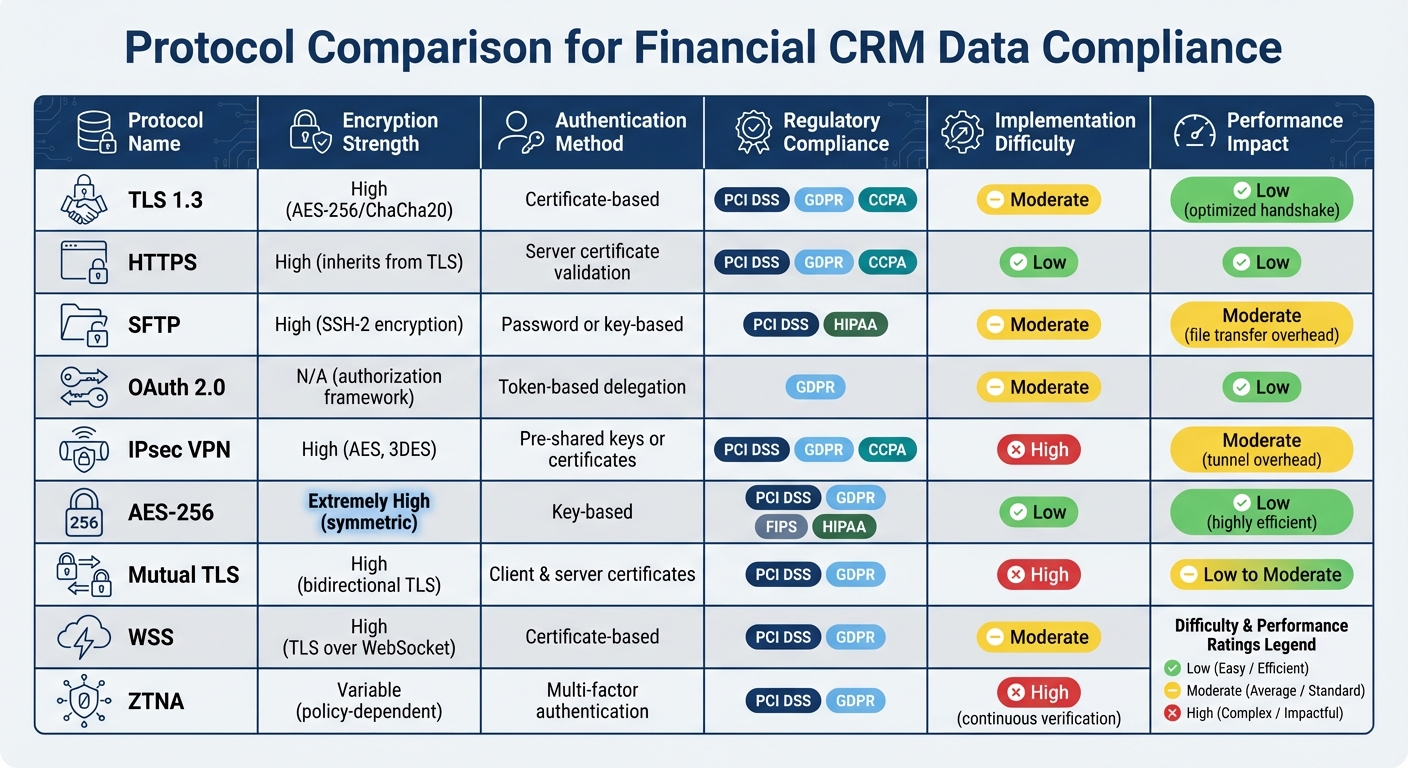
Financial CRM Data Compliance Protocols Comparison Chart
When choosing a protocol, it’s essential to weigh security, performance, and compliance needs. The table below offers a detailed side-by-side comparison of various protocols to help identify the right fit for your requirements.
| Protocol | Encryption Strength | Authentication Method | Regulatory Compliance | Implementation Difficulty | Performance Impact |
|---|---|---|---|---|---|
| TLS 1.3 | High (AES-256/ChaCha20) | Certificate-based | PCI DSS, GDPR, CCPA | Moderate | Low (optimized handshake) |
| HTTPS | High (inherits from TLS) | Server certificate validation | PCI DSS, GDPR, CCPA | Low | Low |
| SFTP | High (SSH-2 encryption) | Password or key-based | PCI DSS, HIPAA | Moderate | Moderate (file transfer overhead) |
| OAuth 2.0 | N/A (authorization framework) | Token-based delegation | GDPR (access control) | Moderate | Low |
| IPsec VPN | High (AES, 3DES) | Pre-shared keys or certificates | PCI DSS, GDPR, CCPA | High | Moderate (tunnel overhead) |
| AES-256 | Extremely High (symmetric) | Key-based | PCI DSS, GDPR, FIPS, HIPAA | Low | Low (highly efficient) |
| Mutual TLS | High (bidirectional TLS) | Client & server certificates | PCI DSS, GDPR | High | Low to Moderate |
| WSS | High (TLS over WebSocket) | Certificate-based | PCI DSS, GDPR | Moderate | Low (real-time efficiency) |
| ZTNA | Variable (policy-dependent) | Multi-factor authentication | PCI DSS, GDPR | High | Moderate (continuous verification) |
This comparison highlights the strengths and challenges of each protocol. For instance, AES-256 is highly efficient for encrypting data at rest, while TLS 1.3 strikes a great balance between security and speed for data in transit. As Emrick Etheridge, an Information Security Expert at DataGuard, explains:
"Encryption serves as your first line of defense against data leaks... especially for industries that handle sensitive data, such as finance" [1].
If regulatory compliance is a top priority, ZTNA and Mutual TLS offer robust access control mechanisms, though they come with higher implementation complexity. For applications where performance is critical, HTTPS and WSS stand out due to their minimal overhead. On the other hand, protocols like IPsec VPN and ZTNA require more intricate setups but deliver strong protection.
Ultimately, the right protocol depends on your organization’s specific needs, especially in industries like finance, where compliance and security are non-negotiable.
To safeguard customer data, financial CRMs need to rely on secure protocols that encrypt information both during transmission and while stored. This is not just a best practice - it’s a necessity. Recent data breaches have highlighted the steep penalties for failing to comply with these standards [3][1].
Strong encryption protocols do more than just ward off breaches; they also help maintain compliance. A single incident of unauthorized data loss can severely harm a financial institution’s reputation, financial stability, and trustworthiness [2]. On top of that, regulatory requirements demand prompt breach notifications to agencies like the FTC, adding another layer of responsibility [3].
Beyond encryption, a thorough risk assessment can further fortify your CRM’s security. Make sure your system includes key measures like TLS 1.3, AES-256 encryption, multi-factor authentication, and continuous monitoring. Regularly evaluate the security of third-party integrations and conduct routine tests to uncover potential vulnerabilities. These steps collectively create a more resilient defense for your CRM.
TLS 1.3 is a transport-layer security protocol designed to provide encrypted communication, stronger authentication, and faster performance. It achieves this by incorporating advanced features like mandatory forward secrecy and eliminating outdated ciphers. On the other hand, HTTPS refers to HTTP traffic that’s secured through a TLS protocol, regardless of the version being used.
When it comes to financial CRM data compliance, the TLS version in use is what truly matters. TLS 1.3 offers the level of security necessary to meet stringent compliance standards. While HTTPS ensures secure transmission of HTTP, it doesn’t specify the encryption strength. For the best protection and compliance, using HTTPS paired with TLS 1.3 is strongly advised.
Zero Trust Network Access (ZTNA) strengthens the security of financial CRM systems by replacing the old "trusted network" model with a "never trust, always verify" mindset. Instead of granting users broad access to the network, ZTNA evaluates and authenticates every request based on factors such as device health, user role, and location. By enforcing least-privileged access policies, it ensures users only access the specific CRM applications they need, reducing the risk of unauthorized access and stopping attackers from moving freely within the system.
For the financial sector, ZTNA plays a crucial role in protecting sensitive client information, complying with regulations like FFIEC authentication, and managing risks associated with third-party access. It continuously verifies identities and permissions, lowering the chances of data breaches while providing detailed access logs to support compliance audits. ZTNA also addresses modern security needs for remote work by offering application-specific access, keeping the broader corporate network secure and out of reach.
AES-256 is a symmetric encryption standard endorsed by NIST, utilizing a 256-bit key to provide an extremely high level of data protection. Its primary strength lies in its ability to withstand brute-force attacks, making it nearly impossible to break with today’s technology.
This robust security is especially important for financial CRMs, where compliance with strict industry regulations is non-negotiable. It also plays a crucial role in protecting sensitive customer and business data from unauthorized access.